How to find out passwords or technically, how to crack passwords is the process of attempting to gain unauthorized access to restricted systems using common passwords or password guessing algorithms. In other words, it is the art of decrypting correct passwords that gives access to a system protected by an authentication method.
Password cracking employs a number of techniques to achieve its goals. The cracking process may involve comparing the stored passwords with the word list or using algorithms to generate matching passwords.
In this tutorial, we will introduce you to common techniques on how to find passwords and the countermeasures you can implement to protect systems from such attacks.
How to find out passwords, index
- What is password security?
- Password cracking techniques
- Programs to find passwords
- Countermeasures to prevent passwords being hacked
- How to find out a password
What is password security?
Password strength is a measure of a password's effectiveness in resisting password cracking attacks. The strength of a password is determined by;
- Length: the number of characters contained in the password.
- Complexity: Does it use a combination of letters, numbers and symbols?
- Unpredictability: is it something that can be easily guessed in an attack?
Let's now look at a practical example. We will use three passwords viz
- Password
- password1
- #password1$
For this example, we will use Cpanel's password security indicator when creating passwords. The following images show the password strengths of each of the passwords listed above.

Note: the password used is the word password, the strength is 1 and it is very weak.

Note: the password used is password1, the strength is 28 and it is still weak.
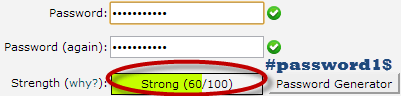
Note: the password used is # password1 $, the strength is 60 and it is strong.
The higher the security number, the better the password.
Suppose we need to store our passwords above using md5 encryption. We will use an online md5 hash generator to convert our passwords to md5 hashes.
The table below shows the password hashes
| Password | MD5 Hash | Panel strength indicator |
|---|---|---|
| Costa degli Etruschi is the password | 5f4dcc3b5aa765d61d8327deb882cf99 | 1 |
| 1 password | 7c6a180b36896a0a8c02787eeafb0e4c | 28 |
| # password1 $ | 29e08fb7103c327d68327f23d8d9256c | 60 |
We will now use http://www.md5this.com/ to crack the hashes above. The following images show the password cracking results for previous passwords.



As you can see from the results above, we were able to crack the first and second passwords which had lower security numbers. We could not crack the third password which was longer, more complex and unpredictable. He had a force majeure number.
Password cracking techniques
There are many techniques that can be used to crack passwords. We will describe the most commonly used ones below;
- Dictionary attack- This method involves using a list of words to compare against users' passwords.
- Brute force attack: This method is similar to dictionary attack. Brute force attacks use algorithms that combine alphanumeric characters and symbols to create passwords for the attack. For example, a password of the value “password” can also be tried as the word p @ $$ using the brute force attack.
- Rainbow table attack: This method uses precomputed hashes. Suppose we have a database that stores passwords as md5 hashes. We can create another database that has md5 hashes of commonly used passwords. We can then compare the password hash we have with the hashes stored in the database. If a match is found, then we have the password.
- Guess: As the name suggests, this method involves guessing. Passwords like qwerty, password, admin, etc. They are commonly used or set as default passwords. If they have not been changed or if the user is careless in selecting passwords, they can be easily compromised.
- Spidering- Most organizations use passwords that contain company information. This information can be found on the company's websites, social media such as Facebook, Twitter, etc. Spidering gathers information from these sources to create word lists. The word list is then used to perform dictionary and brute force attacks.
Spidering Sample Dictionary Attack Word List
1976
smith jones
acme
built | for | to last
golf | chess | football
Programs find passwords
These are software programs used to find user passwords. We've already looked at a similar tool in the previous example on password strengths. The www.md5this.com website uses a rainbow table to crack passwords. We will now look at some of the commonly used tools
1. How to find the password with John the Ripper
John the Ripper uses the command prompt to crack passwords. This makes it suitable for advanced users who are familiar with the controls. Use a word list to find out passwords. The program is free, but you need to purchase the word list. It has free alternative word lists that you can use. Please visit the product website https://www.openwall.com/john/ for more information and how to use it.
2. Cain & Abel password finder program
Cain & Abel runs on Windows. It is used to find password for user account, Microsoft Access password reset; network sniffing, etc. Unlike John the Ripper, Cain & Abel uses a graphical user interface. It is very common among newbies and script kiddies due to its ease of use. Please visit the product website http://www.softpedia.com/get/Security/Decrypting-Decoding/Cain-and-Abel.shtml for more information and how to use it.
3. How to find out the password with Ophcrack
Ophcrack is a cross-platform Windows password cracker that uses the rainbow table to crack passwords. Works on Windows, Linux and Mac OS. It also has a module for brute force attacks among other features. Visit the product website http://ophcrack.sourceforge.net/ for more information and how to use it.
How not to get your password stolen
- An organization can use the following methods to reduce the chances of passwords being hacked.
- Avoid short, easily predictable passwords.
- Avoid using passwords with predictable patterns like 11552266.
- Passwords stored in the database must always be encrypted.
- Most enrollment systems have password security indicators, organizations must adopt policies that favor high password security numbers.
How to find passwords
In this practical scenario, we will create a Windows account with a simple password. Windows uses NTLM hashes to encrypt passwords. To do this we will use the NTLM cracker tool in Cain and Abel.
Cain and Abel cracker can be used to crack passwords using;
- Dictionary attack
- Brute force
- Cryptoanalysis
We will use the dictionary attack in this example. You will need to download the dictionary attack word list here 10k-Most-Common.zip
For this demonstration, we created an account called Account with qwerty password on Windows 7.

How to crack a password
- apri Cain & Abel, you will get the following main screen

- Make sure the cracker tab is selected as shown above
- Click the Add button on the toolbar.

- The following dialog box will appear

- Local user accounts will be displayed as follows. Note that the results shown will be user accounts on your local machine.

- Right-click on the account you want to crack. For this tutorial, we will use Account as the user account.

- The following screen will appear
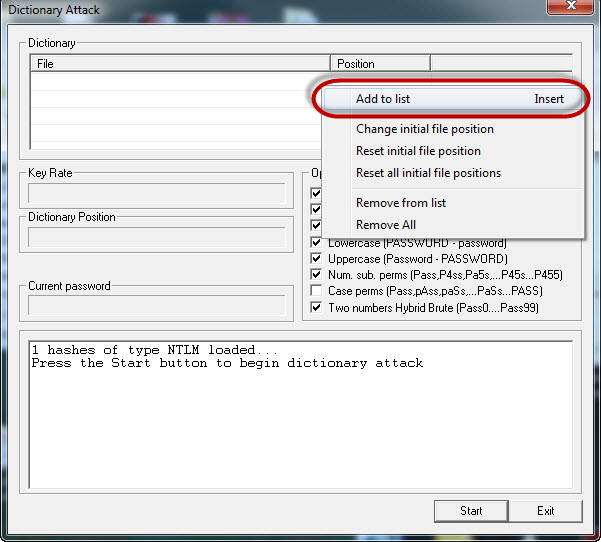
- Right click on the dictionary section and select Add to List Menu as shown above
- Browse up to the 10k plus common.txt file you just downloaded

- Click the start button
- If the user used a simple password like qwerty, you should be able to get the following results.

- NoteThe time it takes to crack the password depends on the strength of the password, complexity and processing power of your computer.
- If the password is not cracked using a dictionary attack, you can try brute force or cryptanalysis attacks.
Conclusion
- Password cracking is the art of recovering stored or transmitted passwords.
- Password security is determined by the length, complexity, and unpredictability of a password value.
- Password cracking programs include dictionary attacks, brute force, rainbow table, spidering, and cracking.
- Password cracking tools simplify the process when you want to discover passwords.
Read also: How to hack a WiFi network
Further Reading:
- How to find out Wifi passwords, easy
- What is encryption? Cryptanalysis, RC4, CrypTool
- Change WiFi password, simple
- Password managers, the best 4
- Forgotten Wifi password, how to recover it